Today more than ever, businesses face a wide range of cybersecurity threats, with social engineering attacks standing out as particularly malicious. These attacks exploit human psychology rather than technical vulnerabilities, making them a significant concern for business owners. Understanding and identifying these deceptive tactics is crucial to safeguarding your organisation’s sensitive information and maintaining trust with clients and partners.
What is a Social Engineering Attack?

Social engineering involves manipulating individuals into divulging confidential information or performing actions that compromise security. Unlike traditional cyberattacks that target system weaknesses, social engineering attacks prey on human tendencies such as trust, curiosity, and fear. Common tactics include phishing, pretexting, baiting, and the promise of free goods/services, all designed to deceive individuals into breaching standard cybersecurity protocols.
The Impact of a Social Engineering Attack on Businesses
The consequences of falling victim to social engineering attacks can be devastating. Financial losses are often immediate, but the ripple effects, such as reputational damage, loss of client trust, and potential legal ramifications, can have long-term impacts on a business’s viability. For instance, a successful phishing attack could lead to unauthorised access to sensitive client data, resulting in data breaches that tarnish the company’s reputation and invite regulatory penalties.
5 Ways to Spot a Social Engineering Attack
Unusual Requests for Sensitive Information
When it comes to social engineering attacks, cybercriminals will often impersonate trusted figures within or associated with your organisation to request confidential data. For example, an employee might receive an email appearing to be from a senior executive urgently requesting access to financial records. Such requests, especially when deviating from standard procedures, should raise immediate suspicion. Always verify the authenticity of the requester through direct communication channels before proceeding.
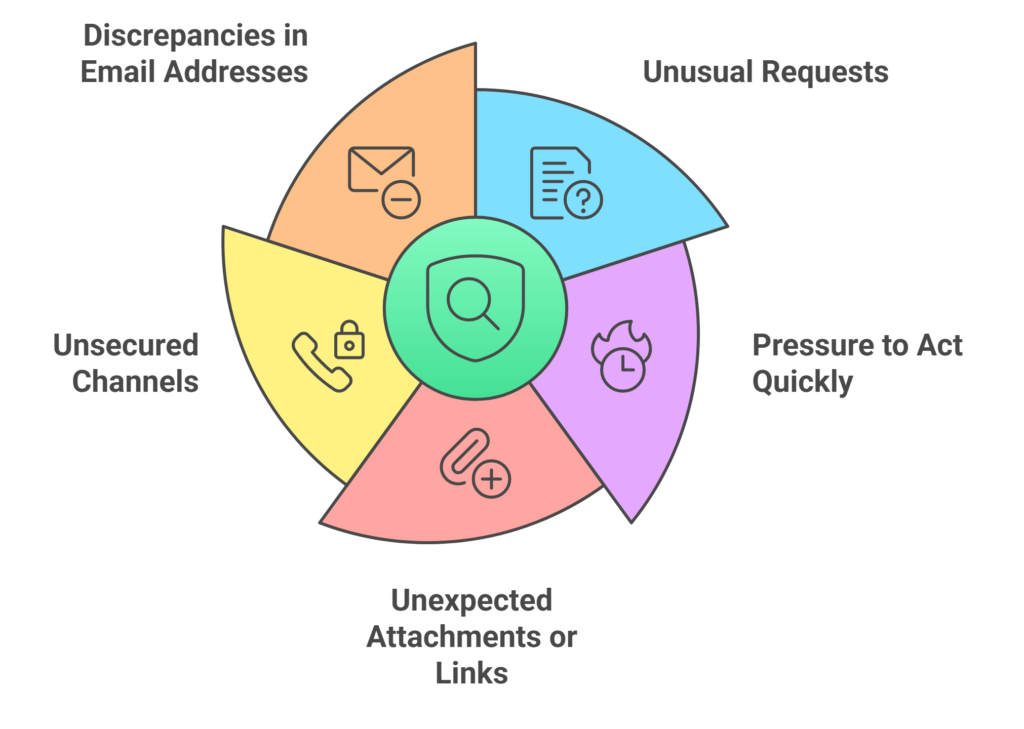
Pressure to Act Quickly
Creating a sense of urgency is a common tactic used to cloud judgment and prompt hasty decisions. An email might threaten account suspension unless immediate action is taken, pressuring the recipient to bypass standard verification processes. It’s essential to approach such demands with caution, taking the time to assess their legitimacy. Legitimate organisations will provide adequate time and will not pressure you into immediate compliance.
Unexpected Attachments or Links
Receiving unsolicited emails with attachments or links, especially from unknown senders, is a red flag. These may contain malware designed to infiltrate your systems. For instance, an email claiming to be an invoice from an unfamiliar supplier might include an attachment that, when opened, installs malicious software. Always scan attachments with up-to-date cybersecurity software and verify the sender’s identity before clicking on any links.
Requests for Confidential Information via Unsecured Channels
Legitimate organisations typically use secure methods to request sensitive data. A phone call or email asking for login credentials or personal information without proper verification is suspect. For example, a caller posing as IT support might request your password to resolve a non-existent issue. Never share sensitive information through unsecured or unsolicited communications. Instead, contact the organisation directly using official channels to confirm the request’s validity.
Discrepancies in Email Addresses or URLs
Attackers often use email addresses or website URLs that closely resemble legitimate ones, with subtle differences. An email might come from “support@yourcompany.co” instead of the official “support@yourcompany.com“. Such minor variations are easy to overlook but can lead to significant security breaches. Always double-check sender information and website URLs for accuracy before engaging.
Steps to Take After Identifying a Social Engineering Attack
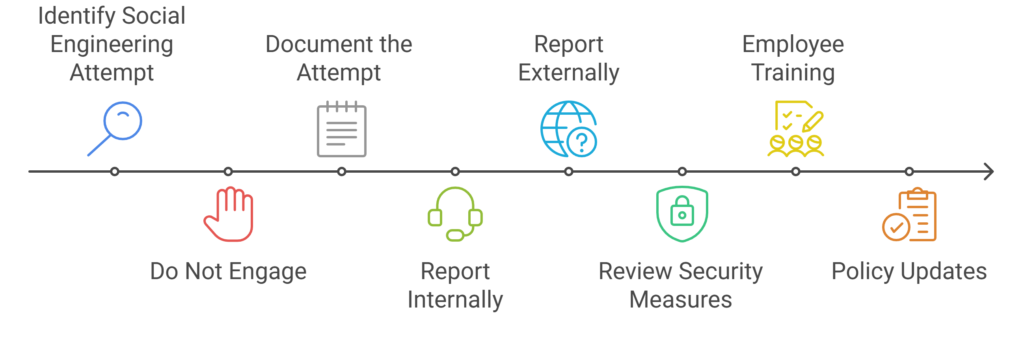
- Immediate Actions
- Do Not Engage: Avoid responding to the attacker, as any interaction can provide them with additional information or encouragement.
- Document the Attempt: Preserve all evidence of the attack, including emails, screenshots, and any other relevant information. This documentation is vital for internal investigations and reporting to authorities.
- Report the Incident
- Internal Reporting: Notify your IT department or security team immediately. Prompt reporting allows for swift action to mitigate potential damage and to strengthen defences against future attacks.
- External Reporting: Inform relevant authorities or cybersecurity organisations. In Australia, entities like the Australian Cyber Security Centre (ACSC) provide guidance and support for businesses facing cyber threats.
- Review and Strengthen Security Measures
- Employee Training: Regularly educate staff about the latest social engineering tactics and prevention strategies. Awareness is a powerful tool in preventing successful attacks. Adept IT Solutions provides professional and effective Cybersecurity Awareness Education and Training.
- Policy Updates: Implement and enforce strict protocols for information sharing and verification. Ensure that all employees are aware of and adhere to these policies to maintain a robust cybersecurity posture.
Additional Cybersecurity Resources for Business Owners

- Educational Materials
- Webinars and Workshops: Managed IT Services, such as the ones offered by Adept IT Solutions, offer cybersecurity awareness sessions tailored to businesses, providing insights into current threats and defence mechanisms.
- Online Courses: Whilst it is all well and good to read about cybersecurity, the dangers of cyberattacks, and how it can impact your business, having a regular course that tests your employee’s knowledge is crucial. Adept IT Solutions offers such a service to businesses, to ensure their staff is prepared for potential cyberattacks.
- Tools and Software
- Security Software: Invest in managed service providers, such as Adept IT Solutions, who instil reputable antivirus and anti-phishing tools to provide an additional layer of defence against malicious attacks.
- Password Managers: Utilise secure password management solutions to ensure that all access credentials are robust and stored safely.
How Adept IT Solutions can Assist with Preventing Social Engineering Attacks
Cyber threats are becoming increasingly sophisticated as each year passes, meaning the vigilance against social engineering attacks is paramount. By recognising the signs and implementing proactive measures, businesses can protect their assets and maintain the trust of their stakeholders. Continuous education, robust policies, and the utilisation of advanced security tools are essential components of a comprehensive defence strategy against these deceptive attacks.
Adept IT Solutions, with over 20 years of experience providing an extensive list of services to clients in Newcastle, Sydney, and beyond, are well equipped to assist your business today. Preparation is key in the cybersecurity world, and our team can ensure that your staff is best set up for success when it comes to safety against social engineering attacks.
If you are ready to experience the IT support and services that your business deserves, contact us today! You can get in touch via phone at 1300 423 378 or email us at info@adept-it.com.au.

